FreeBSDKerberos
用戶添加完成以後進行本地測試。
hawk# kinit cnhawk/
[email protected] cnhawk/
[email protected]'s Password:
hawk# klist -f
Credentials cache: FILE:/tmp/krb5cc_0
Principal: cnhawk/
[email protected] Issued Expires Flags Principal
Jun 7 17:12:21 Jun 8 03:12:21 I krbtgt/
[email protected] 我們可以看到本地已經拿到票據了。
下面添加測試機B的域名地址信息,就是允許測試機B能登陸測試機A。 特別注意Kerberos必須使用域名來訪問機器。如果使用IP添加主機會出現一些意外的問題。
test1# kadmin -l
kadmin> add --random-key host/test1.the9.com //說明添加的是主機不是用戶
Max ticket life [1 day]:
Max renewable life [1 week]:
Principal expiration time [never]:
Password expiration time [never]:
Attributes []:
kadmin> ext host/test1.the9.com
kadmin> ext --keytab=/tmp/the9.keytab host/test1.the9.com
這樣完成以後就好了,基本配置已經結束了,可以使用。
調試
我們開始使用Kerberos的認證部署網絡服務,注意Kerberos通過修改用戶主目錄下的.klogin和.k5login文件,將你允許登陸的用戶Principal添加在文件裡就好了。
test1# cat .k5login
# $FreeBSD: src/etc/root/dot.k5login,v 1.1 2003/04/30 20:58:49 markm Exp $
#
# user1/
[email protected] # user2/
[email protected] cnhawk/
[email protected] 這樣就可以了
使用Kerberos認證的telnet
修改/etc/inetd.conf 添加
telnet stream tcp nowait root /usr/libexec/telnetd telnetd -a user
然後開啟
test2# inetd
然後從test1登陸test2
test1# kinit cnhawk/test1.the9.com //先取得票據
cnhawk/
[email protected]'s Password:
test1# klist –f //看看是不是取得
Credentials cache: FILE:/tmp/krb5cc_0
Principal: cnhawk/
[email protected] Issued Expires Flags Principal
Jun 11 16:21:36 Jun 12 02:21:36 I krbtgt/
[email protected] //可以了
test1# telnet -a -l the9 192.168.0.3 //開始登陸
Trying 192.168.0.3...
Connected to test2.the9.com.
Escape character is '^]'.
[ Trying mutual KERBEROS5 (host/
[email protected])... ]
[ Kerberos V5 accepts you as `` cnhawk/
[email protected]'' ]
FreeBSD/i386 (test2.the9.com) (ttyp1)
//登陸歡迎詞
%id
uid=1001(the9) gid=0(wheel) groups=0(wheel)
% //好了成功了
使用Kerberos認證的ssh
修改測試A,B,C的sshd 配置文件。
# Kerberos options
KerberosAuthentication yes
KerberosOrLocalPasswd yes
然後重啟sshd
Test2#kill –HUP 80
開始從test1登陸到test2,因為只有ssh1支持Kerberos,所以使用ssh1連接同時開啟debug信息。
test1# ssh -1v
[email protected] OpenSSH_3.6.1p1 FreeBSD-20030924, SSH protocols 1.5/2.0, OpenSSL 0x0090703f
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: Rhosts Authentication disabled, originating port will not be trusted.
debug1: Connecting to test2.the9.com [192.168.0.3] port 22.
debug1: Connection established.
debug1: identity file /root/.ssh/identity type -1
debug1: Remote protocol version 1.99, remote software version OpenSSH_3.5p1 FreeBSD-20030924
debug1: match: OpenSSH_3.5p1 FreeBSD-20030924 pat OpenSSH*
debug1: Local version string SSH-1.5-OpenSSH_3.6.1p1 FreeBSD-20030924
debug1: Waiting for server public key.
debug1: Received server public key (768 bits) and host key (1024 bits).
debug1: Host 'test2.the9.com' is known and matches the RSA1 host key.
debug1: Found key in /root/.ssh/known_hosts:3
debug1: Encryption type: 3des
debug1: Sent encrypted session key.
debug1: Installing crc compensation attack detector.
debug1: Received encrypted confirmation.
debug1: Trying Kerberos v5 authentication.
debug1: Kerberos v5 authentication accepted.
debug1: Requesting pty.
debug1: Requesting shell.
debug1: Entering interactive session.
Last login: Fri Jun 11 16:31:14 2004 from test1.the9.com
Copyright (c) 1980, 1983, 1986, 1988, 1990, 1991, 1993, 1994
The Regents of the University of California. All rights reserved.
FreeBSD 4.9-RELEASE (GENERIC) #0: Mon Oct 27 17:51:09 GMT 2003
FreeBSD/i386 (test2.the9.com) (ttyp1)
//登陸歡迎詞
%id
uid=1001(the9) gid=0(wheel) groups=0(wheel)
% //好了成功了
測試已經完成了。可以使用Kerberos了。
ftp 服務
%kinit cnhawk/test1.the9.com
Cnhawk/test1.the9.com @THE9.COM's Password:
%klist -f
Credentials cache: FILE:/tmp/krb5cc_1001
Principal: cnhawk/
[email protected] Issued Expires Flags Principal
Jun 11 18:49:56 Jun 12 04:49:56 I krbtgt/
[email protected] %/usr/local/bin/ftp -v hawk.the9.com
Connected to hawk.the9.com.
220 hawk.the9.com FTP server (Version 5.60) ready.
334 Using authentication type GSSAPI; ADAT must follow
GSSAPI accepted as authentication type
GSSAPI authentication succeeded
Name (hawk.the9.com:cnhawk):
232 GSSAPI user
[email protected] is authorized as cnhawk
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
好了FTP也可以接受登陸
總結 Kerberos使用中需要注意一些地方,例如,時間一定要保證同步,因為Kerberos靠時間戳來保持同步,時間允許的飄溢量非常小。所以必須保證時間的准確。
cnhawk# kinit cnhawk/
[email protected] cnhawk/
[email protected]'s Password: kinit: krb5_get_init_creds: time skew (314) larger than max (300) cnhawk# ntpdate time.the9.com 7 Jun 16:59:49 ntpdate[623]: step time server 61.129.93.5 offset 211.348035 sec cnhawk# kinit cnhawk/test1.the9.com @THE9.COM cnhawk/
[email protected]'s Password:
而且很多時候在登陸前要查看票據是不是過期了。
hawk# klist Credentials cache: FILE:/tmp/krb5cc_0 Principal: cnhawk/
[email protected] Issued Expires Principal
Jun 7 17:19:25 >>>Expired<<< krbtgt/
[email protected] Jun 7 17:20:23 >>>Expired<<< host/
[email protected] 同時要注意認證時候不只是認證用戶信息,還有主機信息,要保證這兩個信息都在KDC中心數據庫上存儲。這樣才能保證用戶取得票據以後能順利登陸服務器。
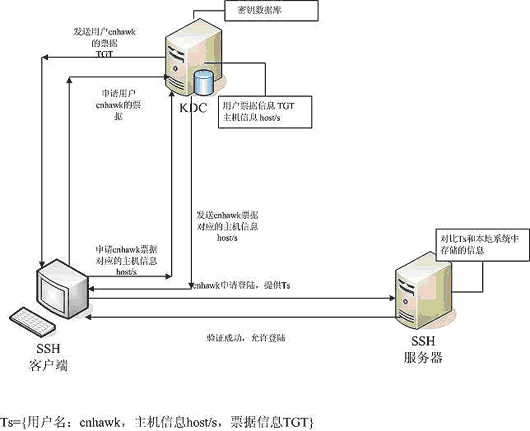
Kerberos系統認證過程示意圖